While most applications require authentication to gain access to private information or to execute tasks, not every authentication method is able to provide adequate security. Negligence, ignorance, or simple understatement of security threats often result in authentication schemes that can be bypassed by simply skipping the log in page and directly calling an internal page that is supposed to be accessed only after authentication has been performed.
In addition, it is often possible to bypass authentication measures by tampering with requests and tricking the application into thinking that the user is already authenticated. This can be accomplished either by modifying the given URL parameter, by manipulating the form, or by counterfeiting sessions.
In this Write-Up i’ll describe how i hacked BillMeLater’s Merchant Launch Site logging into Admin Account exploiting an Authentication Bypass Vulnerability and what this bug allowed me to do once logged in.
Steps required to reproduce the issue:
After some DNS-bruteforcing i found this BillMeLater’s subdomain:
https://launch.billmelater.com
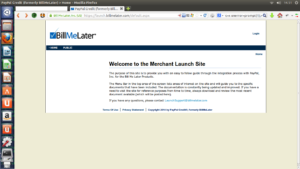
Once clicked on “Login” i have been redirected to https://launch.billmelater.com/Home/tabid/36/ctl/Login/Default.aspx?returnurl=/default.aspx
so i started playing with this URL deleting “?returnurl=/default.aspx” from the URL above.
So this is the New URL:
https://launch.billmelater.com/Home/tabid/36/ctl/Login/Default.aspx
My attention was attracted by the “Login” directory so i started to manually fuzz the URL changing “Login” with “Register”
https://launch.billmelater.com/Home/tabid/36/ctl/Register/Default.aspx
Once submitted the request i received a “302” Status code so the link is accessible only if logged in.
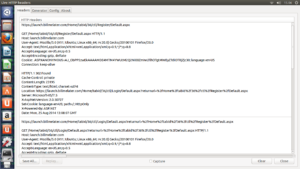
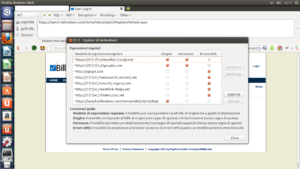
So i thought to use a Mozilla Firefox add-on called “NoRedirect” to not redirects me to the login page.
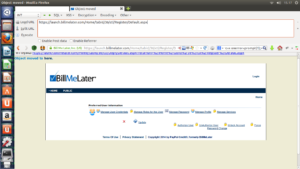
Now if i go to https://launch.billmelater.com/Home/tabid/36/ctl/Register/Default.aspx i will be logged in as Administrator and i can execute operations like if i were the Administrator.
Now the bug has been fixed and here’s a video of the process of exploiting this vulnerability:

